Data-Stealing Chrome Extensions Are Impersonating Trusted Brands — Here’s What You Need to Know

In a newly uncovered cybercrime campaign, more than 100 malicious Chrome extensions have been discovered targeting users across the globe. These extensions disguise themselves as trustworthy tools, impersonating brands like Fortinet, YouTube, DeepSeek AI, and various popular VPN services. Behind the scenes, however, they are designed to exfiltrate sensitive data, manipulate traffic, and grant attackers control over browser sessions.
This disturbing development sheds light on an often-overlooked threat vector: the browser extension. Long considered harmless add-ons that enhance productivity or provide niche functionality, extensions are now being weaponized with alarming effectiveness. And what’s even more concerning is how authentic these malicious tools appear.
A Campaign Built on Deception
These malicious extensions have been distributed through a network of carefully crafted domains, many of which mimic real products or services. Domains like forti-vpn[.]com, youtube-vision[.]com, and deepseek-ai[.]link aim to build trust by associating themselves with legitimate brands and tools. Unsuspecting users, seeking enhanced VPN services or smarter AI tools, are lured in by these professional-looking websites and Chrome Web Store listings.
Once installed, the extensions initiate communication with remote servers under the attackers’ control. From there, the browser becomes a compromised environment. These tools quietly harvest authentication cookies, session tokens, and other valuable information. With access to these credentials, attackers can hijack user sessions, impersonate identities, and gain unauthorized access to sensitive accounts.
But the capabilities don’t stop at surveillance. The extensions are designed to receive and execute commands in real time. This means attackers can alter network behavior, redirect users to phishing pages, inject malicious ads, or even proxy traffic through the infected machine—all without the user’s knowledge.
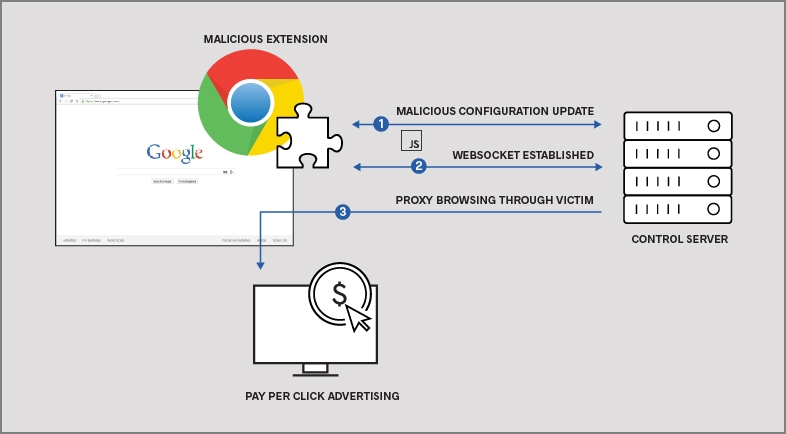
Why This Threat Is So Dangerous
What makes this campaign particularly troubling is its blend of stealth and believability. Unlike crude scams or obvious malware, these extensions often provide partial functionality, creating a sense of legitimacy. A Fortinet-branded VPN tool might establish a secure-looking tunnel; a YouTube enhancer may tweak video settings as promised. Yet behind these features lies a sophisticated mechanism for data theft.
These attacks are especially dangerous in corporate environments, where a compromised browser could provide a backdoor into business applications, email systems, customer data platforms, and beyond. Because many organizations don’t tightly manage browser extensions, employees can unknowingly open the door to severe breaches simply by installing what looks like a helpful plugin.
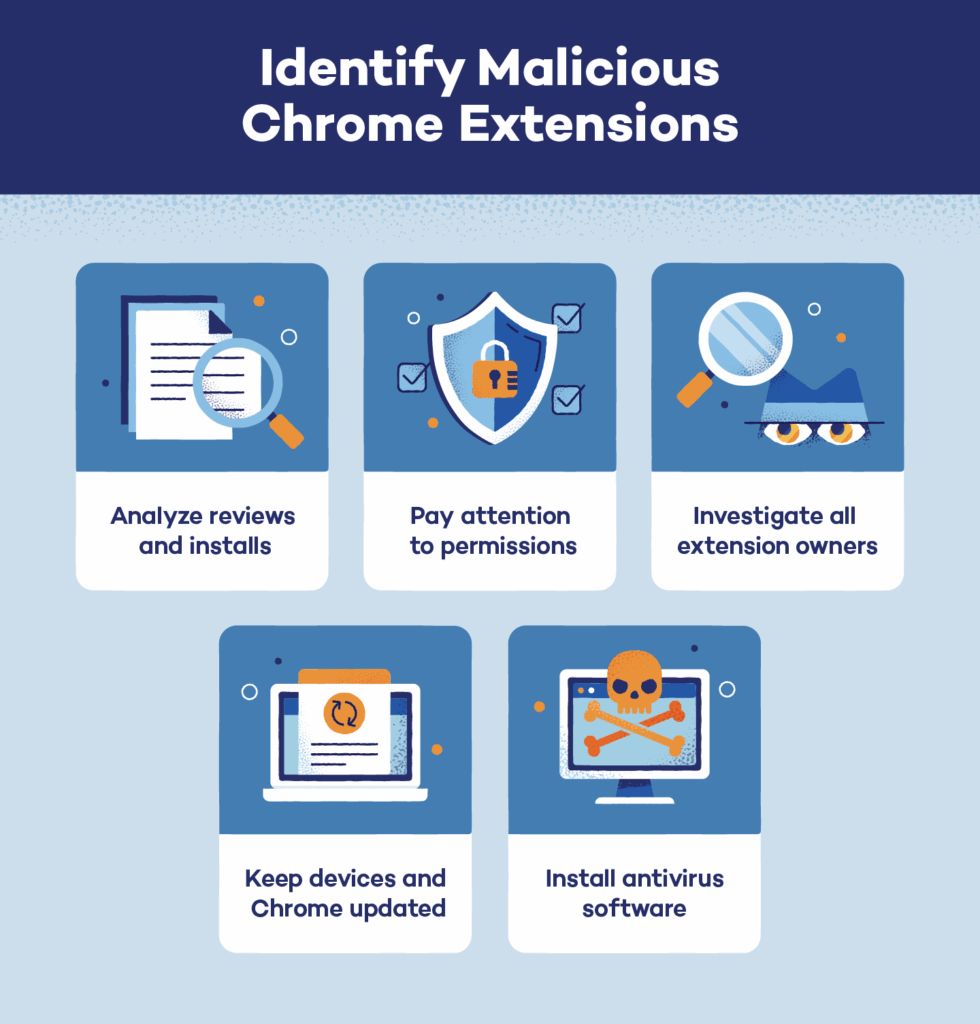
What Can Be Done to Mitigate the Risk?
The good news is that this type of threat can be mitigated with the right combination of technology, policy, and awareness. First and foremost, organizations should consider implementing browser management policies that limit which extensions can be installed. Chrome, for instance, provides enterprise controls that allow administrators to pre-approve trusted extensions while blocking all others.
Regular audits of installed extensions should also be part of any organization’s security routine. Employees should be encouraged—or even required—to report unknown or newly installed extensions for review. In parallel, IT teams should monitor outbound network activity, paying close attention to connections to suspicious or rarely used domains.
Employee education is another critical component. Many users still assume that anything found on the Chrome Web Store is inherently safe. But as this campaign demonstrates, even listings that seem polished and reputable can be harmful. Training sessions and internal awareness campaigns can help shift this mindset and empower employees to make safer choices.
Finally, organizations should consider browser security as part of a broader zero trust architecture. Just as we no longer assume that users within the corporate network are automatically trustworthy, we must stop assuming that browser-based activity is safe by default.
A Wake-Up Call for Browser Security
This latest campaign serves as a powerful reminder that the humble browser extension is no longer just a productivity tool—it’s a potential threat vector with serious consequences. As attackers grow more sophisticated, defenders must evolve as well. It’s not enough to guard the network perimeter or monitor endpoint behavior. Security teams must now extend their focus to the software running within the browser itself.
For companies and users alike, vigilance is key. The next time you’re prompted to install a Chrome extension—whether it’s a VPN tool, an AI assistant, or a YouTube enhancer—pause and verify. The price of convenience could be your data, your identity, or your business’s security.
At AWSMTECH, we help organizations stay ahead of evolving cybersecurity threats. If you’d like assistance in reviewing your browser security policies, implementing extension controls, or simply assessing your current exposure, our team is here to support you.


